Hi friends today we will show you how to hack an friend's PC using an key logger.Key logger are the set of codes which can be used to record the keystrokes of PC by directly stealing the input from Kernel. In this tutorial we will show you how to make an Key logger file using a revolutionary software PROJECT NEPTUNE V1.78 key logger which is available as both freeware & shareware.
http://trojansecrypters.blogspot.com/2011/03/project-neptune-keylogger-tutori...
or
http://www.4shared.com/file/84ggi8v6/Project_Neptune_v145b.html
or
http://www.mediafire.com/?roo61g3sias9oy8
Step 1:Download this Neptune key logger from any of these links
http://trojansecrypters.blogspot.com/2011/03/project-neptune-keylogger-tutori...
or
http://www.4shared.com/file/84ggi8v6/Project_Neptune_v145b.html
or
http://www.mediafire.com/?roo61g3sias9oy8
Step 2: open Project Neptune v1.78 from the downloaded files

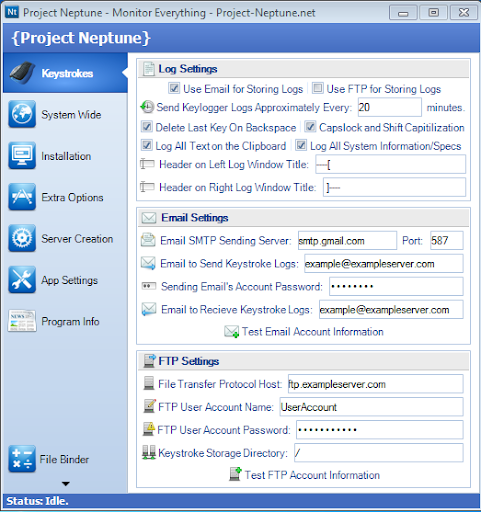
Step 3: In email settings enter your email id in “ENTER EMAIL TO SEND KEYSTROKE LOGS”(this id should be your "fake id" since generally email service providers recognize them as spam and delete them in 7 days)
Step 4: Provide your password in “SENDING EMAIL ACCOUNTS PASSWORD”
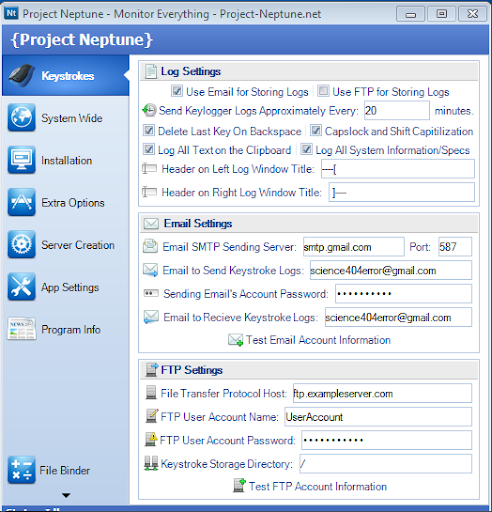
Step 5: provide your same email ID or different ID where you want to receive (ex:science404error@gmail.com)

Also if you have known about FTP and have a FTP account you can use that too.
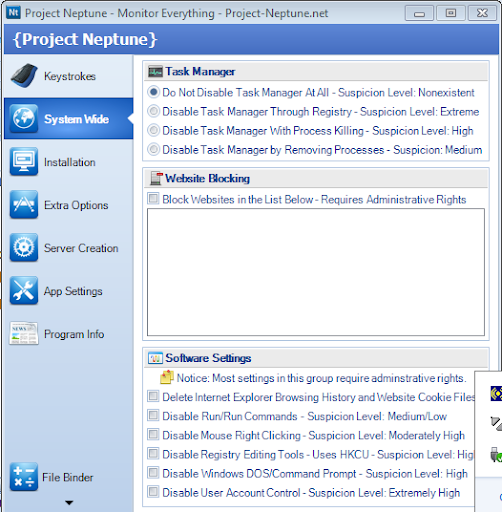
Step 6 (optional): If you want to disable mouse clicking /Internet explorer/Registry commands/Run dialog box/Task manger you can do that through going to “SYSTEM WIDE “ tab and checking the necessary check boxes. You can also prevent user from accessing specific websites (ex :any online scanners)

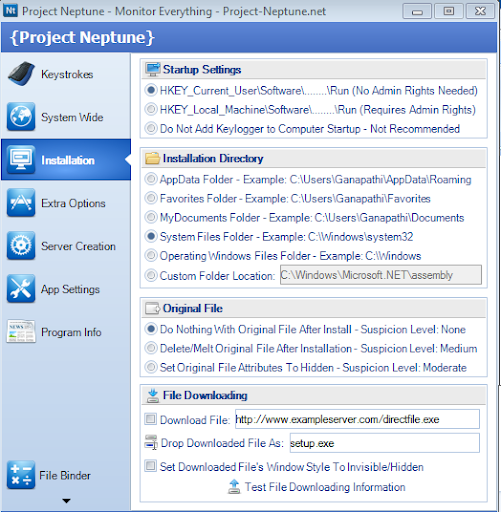
Step 7: In Installation tab you can specify the directory where your key logger is going to RUN on your friends PC .It is best to select “system Files Folder-C:\windows\system32”

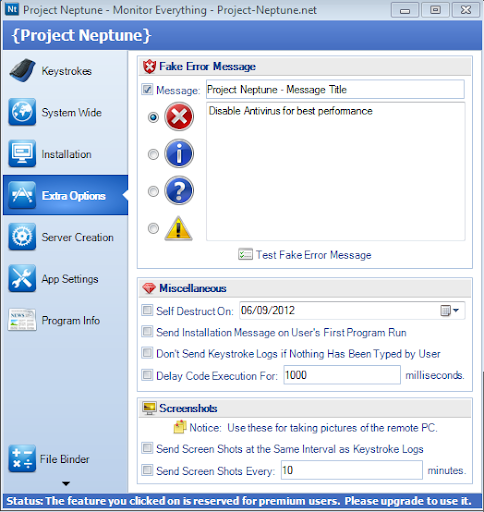
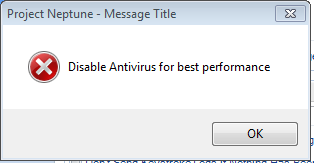
Step 8(optional): Using “EXTRA OPTIONS” tab you can display an fake error messages like “Disable Antivirus for best performance”. Also using this tab we can destroy our own key logger files after certain period of time.

During execution the error message will be displayed as

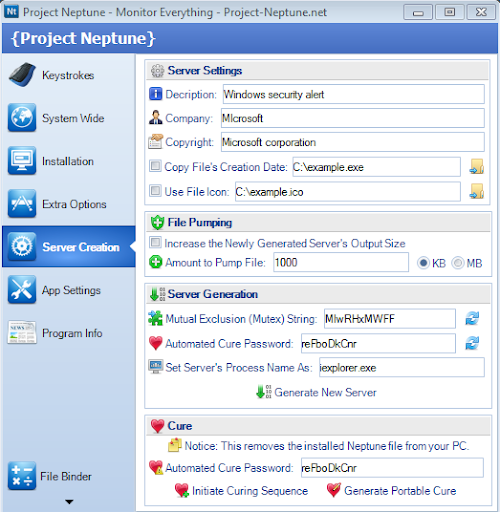
Step 9:The most important step in this process is server creation which needs bit logic .Go to “Server creation” tab on server settings type the required description ,Company,Copyright. for ex
Description: windows security alert
Company: Microsoft
Copyright: Microsoft Corporation
You can provide anything but it must be "doubtless" in regarding because these details will be displayed at task manager during execution
Step 10: Next on “server generation” provide any name to your key logger file (ex:iexplorer.exe) on “SET SERVER NAME’S PROCESS AS”

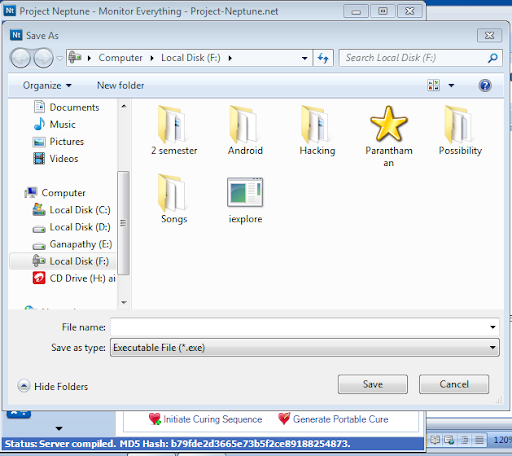
Step 11: Click on “GENERATE NEW SERVER” and save it to desired location.whoa ! you created an keylogger now send that file to victim.

NOTE: these .exe files are easily detectable and cannot be send by gmail, for this purpose try to compile it with any of other games or word documents and send it to your victim.
If you have any clarifications comment on these post and we will try to solve it at best
Stay tuned at science404error.blogspot.in for more upcoming tutorials, Click like on our Facebook page






yeah i love your tut but i do have an issue which i want you to be of help, you see i have done that which you stated here and it's work cos i use it to key log my system and am getting logs of my system but if i try to send it to a victim as an attach file after he or she click it, i still can't get log from the victim please what should i do, your kind responds is highly appreciate, can you give tut on how to bind document files like power point and all that with executable file of keylogger together.
server is not making, its denied for the path :(